A new fake Cloudflare screen is tricking site visitors into running a malicious PowerShell script via Win + R. Here’s what’s really happening and a step-by-step cleanup checklist for website owners.
1. Why you should care
Last week, kennerlys.com.au—the website of an established, trusted Perth accounting practice—suddenly began redirecting every visitor, including Googlebot, to a “Verify you are human” screen.
The page carried Cloudflare’s logo but instead of a normal CAPTCHA it ordered users to press Win + R, paste a mysterious command, and hit Enter. Anyone who complied gave an attacker remote control in under a second. If your site is showing the same screen, the clock is ticking. This guide explains how the scam works, how to protect your visitors, and—crucially—how to scrub the malware from your server in the safest way possible.
2. What the attack looks like
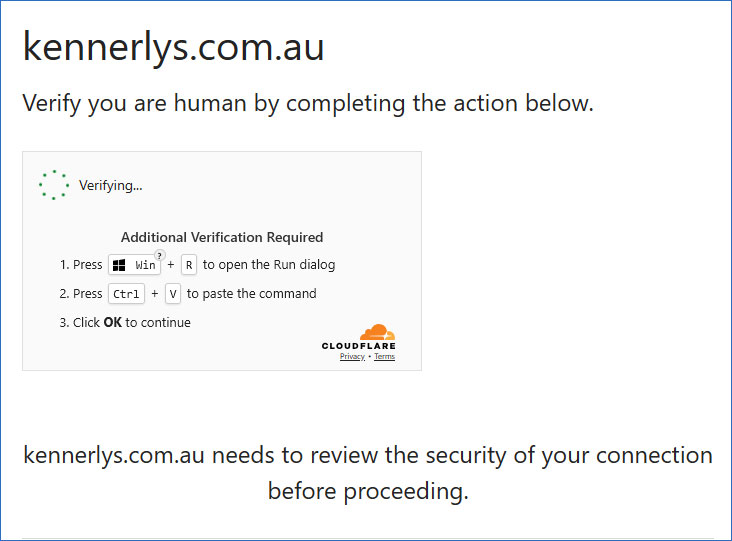
- The page is mostly white with your own domain name in a large heading (e.g.
kennerlys.com.au). - A grey inset box shows a spinning “Verifying…” dot pattern under the heading Additional Verification Required.
- The numbered steps tell the user to
- press Win + R to open the Run dialog,
- press Ctrl + V to paste a command that the site has copied to the clipboard, and
- click OK to continue.
- A miniature Cloudflare logo appears at the bottom of the box to lend false legitimacy.
3. Under the hood: step by step
- 🕵️♂️Obfuscated JavaScript loads the “verification” overlay.
- 📋The script silently copies a one-liner PowerShell payload to the clipboard.
- 💻User pastes it into Win + R; the payload pulls malware straight into memory.
- 🎯A stealer or RAT installs, giving attackers full access.
4. Quick ways to spot the fake
- Any Cloudflare “challenge” that asks for Win + R is guaranteed to be malicious.
- Press Ctrl + V in Notepad—if a long PowerShell string appears, the clipboard has been hijacked.
- Cloudflare’s genuine CAPTCHA lives on challenges.cloudflare.com, never inside your site’s HTML.
5. If you are just a visitor
- Close the tab immediately; do not paste anything.
- Clear your clipboard (copy any harmless word).
- Run a full antivirus scan.
- If you did paste and run the command, change all passwords, enable MFA, and scan for remote-access tools.
6. Incident-response guide for site owners
- Take the site offline. Put it in maintenance mode or protect it with basic auth so crawlers stop indexing the malware.
- Preserve evidence. Zip the entire web root and export database dumps for later forensics.
- Diff files and timestamps. Look for recent changes to
.js,header.php, or any file that suddenly grew larger. - Search for injections. Grep for keywords like
atob(',eval(,Function(, and strange long hex strings. - Patch everything. Update WordPress core, themes, plugins, PHP, and server packages.
- Rotate credentials. Change hosting panel, SSH, SFTP, database, and WordPress admin passwords.
- Scan externally. Use Sucuri SiteCheck, VirusTotal URL, or Wordfence to confirm the site is now clean.
- Request a review. In Google Search Console, click Security Issues & Manual Actions → Request Review so warning pages disappear.
7. Preventive measures
- Enable a web application firewall (Cloudflare WAF, Wordfence, or similar).
- Create least-privilege user roles—editors should not be administrators.
- Set up file-change monitoring; email alerts on any new or modified core files.
- Automate off-server backups (daily files + hourly database).
8. Key takeaways
Be suspicious of any “verification” that leaves the browser. Move fast to protect users and search rankings. Patch, monitor, and keep backups handy.
9. Need expert help?
PcRiot can audit, clean, and harden your site in one session. Book a security check →
Pingback: ClickFix: How Hackers Use ‘Verification’ to Steal Your Information – Fordham University Information Security and Assurance
Comments are closed.